New Stealer Campaign Exploits Windows SmartScreen Vulnerability (CVE-2024-21412) – This large-scale assault targets Windows customers, stealing passwords, searching historical past, and crypto pockets particulars.
FortiGuard Labs has recognized a large-scale stealer marketing campaign focusing on Microsoft Windows customers. This marketing campaign exploits a identified vulnerability (CVE-2024-21412) to bypass safety measures and steal delicate knowledge.
CVE-2024-21412 is a safety bypass vulnerability in Microsoft Windows SmartScreen, a function designed to alert customers to doubtlessly unsafe purposes or web sites. The flaw permits distant attackers to bypass the SmartScreen safety warning dialogue and ship malicious recordsdata.
Over the previous 12 months, a number of attackers, together with Lumma Stealer and Meduza Stealer, have exploited this vulnerability, Fortinet researchers famous.
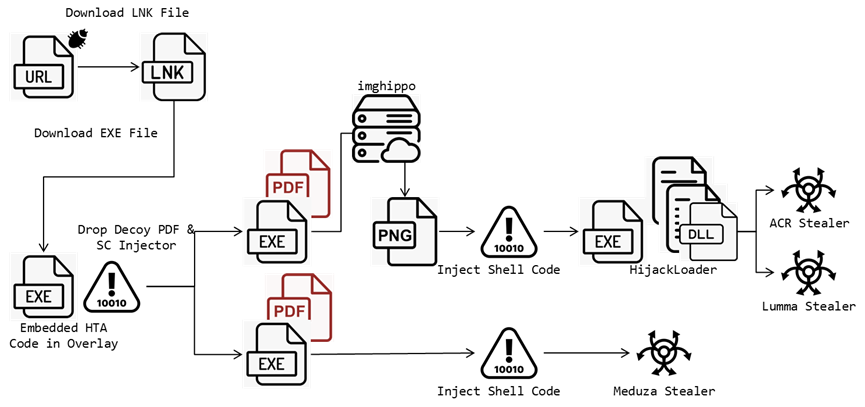
Attack Chain
This marketing campaign, as per FortiGuard Labs’ report shared with Hackread.com forward of publishing on Tuesday, July 23, 2024, spreads a number of recordsdata that exploit CVE-2024-21412 to obtain malicious executable recordsdata. Here is the sequence of assaults.
- Initial Phishing: The marketing campaign begins with a phishing e-mail containing a malicious hyperlink. Clicking the hyperlink downloads a URL file that, in flip, downloads an LNK file.
- LNK File Execution: The LNK file makes use of PowerShell instructions to obtain an HTA script disguised as an overlay icon.
- HTA Script Decodes Payload: The HTA script retrieves and executes a hidden PowerShell script, which runs silently and downloads a decoy PDF and a malicious shell code injector, injecting the ultimate stealer into reliable processes.
- Shellcode Injection: Two kinds of injectors have been recognized. The first injector makes use of a picture file to acquire a shell code, with low detection charges on VirusTotal. The second injector downloads a JPG file from the Imghippo web site and makes use of the Windows API “GdipBitmapGetPixel” to entry pixels and decode bytes to get the shell code. The different injector is extra easy, decrypting its code from the info part and utilizing a collection of Windows API capabilities to carry out shell code injection.
- Stealer Deployment: The injected code downloads and installs information-stealing malware, similar to Meduza Stealer model 2.9 or ACR Stealer.
Stolen Data and Regional Targeting
The ACR Stealer targets numerous purposes, together with browsers, crypto wallets, messengers, FTP purchasers, e-mail purchasers, VPN providers, password managers, and different instruments. The stealer can adapt reliable internet providers to keep up communications with its C2 server. The marketing campaign appears to focus on particular areas, with decoy PDFs tailor-made to North America, Spain, and Thailand.
Implementing Microsoft’s newest safety updates to deal with the CVE-2024-21412 vulnerability is essential to remain protected. Users ought to be cautious of phishing hyperlinks and downloading unknown recordsdata. Email safety options can detect and block phishing makes an attempt. A complete safety suite can present real-time malware safety.
The full listing of focused purposes is accessible right here.
Mr. Ngoc Bui, Cybersecurity Expert at Menlo Security commented on the latest improvement stating,
“The recent discovery of CVE-2024-21412 reveals the persistent and evolving nature of cyber threats targeting Microsoft’s SmartScreen. It demonstrates that attackers are constantly refining their tactics to bypass traditional security measures and deliver malicious payloads to high-value targets. This highlights the need for proactive threat intelligence and layered defences to protect against these sophisticated attacks.”
- Windows Defender Flaw Exploited by Phemedrone Stealer
- Critical New Outlook RCE Vulnerability Exploits Preview Pane
- 7-Year-Old 0-Day in MS Office Exploited to Drop Cobalt Strike
- Black Basta Ransomware Exploited Windows 0-day Before Patch
- Palo Alto Patches 0-Day (CVE-2024-3400) Exploited by Backdoor
- MS Outlook Vulnerability Exploited by Russian Forest Blizzard Group
- Microsoft Releases Tool to Fix CrowdStrike-Caused Windows Chaos
- Russian APT28 Exploiting Windows Vulnerability with GooseEgg Tool





No Comment! Be the first one.