Meet TgRat Trojan: Once recognized for focusing on Windows units, the brand new model targets Linux and runs its command and management heart via the favored messaging app Telegram.
This malware, which permits cybercriminals to remotely management contaminated machines, exfiltrate information, and execute instructions, was initially found in a Windows model two years in the past however has now been tailored to focus on Linux environments.
The TgRat trojan operates by connecting to a Telegram bot, a way that takes benefit of the favored messaging platform’s widespread use in company settings. This distinctive management mechanism permits attackers to problem instructions to the contaminated system secretly, making it tough for victims to detect the an infection.
Upon an infection, TgRat checks to verify it’s working on a focused machine by evaluating the pc’s title hash in opposition to an embedded string. If the values don’t align, the malware self-terminates, avoiding detection. If it does match, the trojan connects to the Telegram bot and awaits additional directions from its operators.
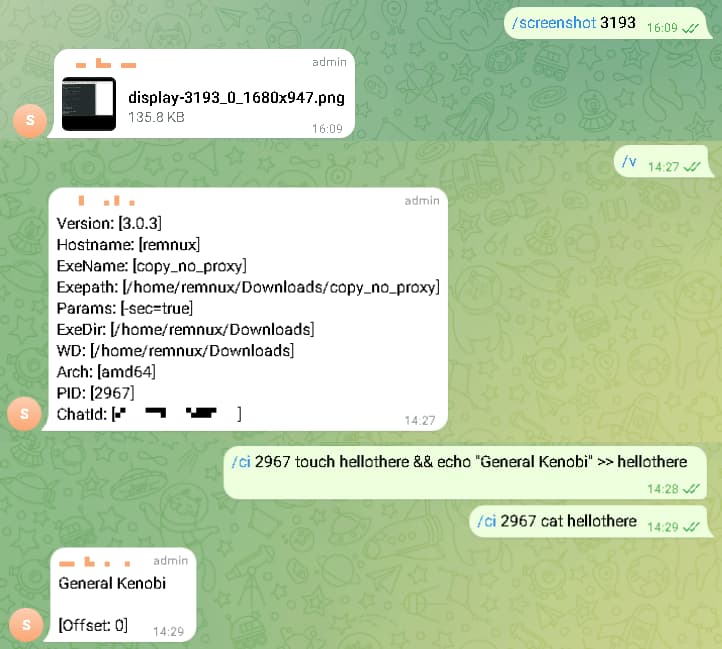
Once established, TgRat can execute numerous malicious actions, together with downloading information, taking screenshots, and working instructions remotely. Its design permits for the execution of whole scripts via a single message, enhancing its effectiveness and stealth.
According to Dr. Web’s weblog publish, the invention got here after a internet hosting supplier reported suspicious exercise, prompting Doctor Web’s virus lab to analyze. They discovered a trojan dropper that put in the TgRat malware on the server, resulting in additional evaluation of its capabilities.
Experts warn that the usage of Telegram for command and management makes this trojan notably stealthy. The common site visitors to Telegram’s servers can simply disguise malicious communications, complicating detection efforts for community safety groups.
While the TgRat trojan is a classy risk, cybersecurity professionals can establish its exercise by monitoring community site visitors. Unusual exchanges with Telegram servers from native community units can sign a possible compromise, permitting for well timed intervention.
- Phishers Now Actively Automating Scams with Telegram
- Telegram Android Flaw “EvilVideo” Sends Malware as Videos
- Triada Malware Infects Android Devices by way of Fake Telegram App
- Telekopye Toolkit Used as Telegram Bot to Scam Marketplace Users
- Chinese APT Slid Fake Signal, Telegram Apps onto Official App Stores




No Comment! Be the first one.