
Again in Could, Microsoft started establishing new accounts to be passwordless by default. Instead of passwords, the corporate pushed customers in the direction of choices like passkeys and Home windows Hey.
Now, German researchers Tillmann Osswald and Dr. Baptiste David have revealed at this 12 months’s Black Hat convention in Las Vegas how the enterprise model of Home windows Hey will be cracked.
Throughout their dwell demonstration, Osswald and David confirmed simply how dangerous it’s. After David logged into his machine utilizing his personal face, Osswald, performing because the attacker with native admin entry, merely ran just a few strains of code. He then injected his personal facial scan, captured on a distinct laptop, into the goal machine’s biometric database. Seconds later, He leaned in, and the pc put up no resistance and unlocked for him immediately, accepting his face as if it had been David’s all alongside.
To grasp how this works, it’s a must to have a look at the internals. The way in which Home windows Hey works in a enterprise setting is that when it’s first provisioned, a public/non-public key pair is generated. That public key’s then registered with the group’s ID supplier, like Entra ID.
The biometric knowledge itself, nevertheless, is saved in a database managed by the Home windows Biometric Service (WBS), and this database is encrypted. Then, upon authentication, the system matches the dwell scan to the saved template.
The issue is that in some implementations, the encryption defending that database can’t cease an attacker who has already gained native admin privileges, permitting them to decrypt the biometric knowledge.
Enter Enhanced Signal-in Safety (ESS), Microsoft’s reply to the issue that works by isolating your complete biometric authentication course of inside a safe atmosphere managed by the system’s hypervisor.
However, there is a catch, after all. For ESS to work, a machine wants a really particular set of {hardware}: a contemporary 64-bit CPU that helps {hardware} virtualization (since ESS is constructed on Virtualization-Based mostly Safety), a TPM 2.0 chip, Safe Boot enabled within the firmware, and specifically licensed biometric sensors. Facet observe: Microsoft mandates this degree of safety for its new line of Copilot+ PCs, however as Osswald notes, many current computer systems fall quick.
ESS could be very efficient at blocking this assault, however not everybody can use it. For instance, we purchased ThinkPads round one and a half years in the past, however sadly they don’t have a safe sensor for the digicam as a result of they use AMD chips and never Intel’s.
Okay, so we’ve got an issue. How can we repair it? In response to Osswald and David, a correct patch could be very “tough” and even inconceivable to implement and not using a large redesign, as a result of it hits the basic structure of how non-ESS programs retailer that biometric knowledge.
For now, in case you are on a enterprise machine utilizing Home windows Hey with out ESS, they suggest that you simply disable the biometrics fully and use one thing like a PIN as a substitute.
The simplest method to verify in case your machine helps ESS is to go to your system settings. In your account’s “Signal-in choices”, you might discover a toggle labeled “Check in with an exterior digicam or fingerprint reader”.
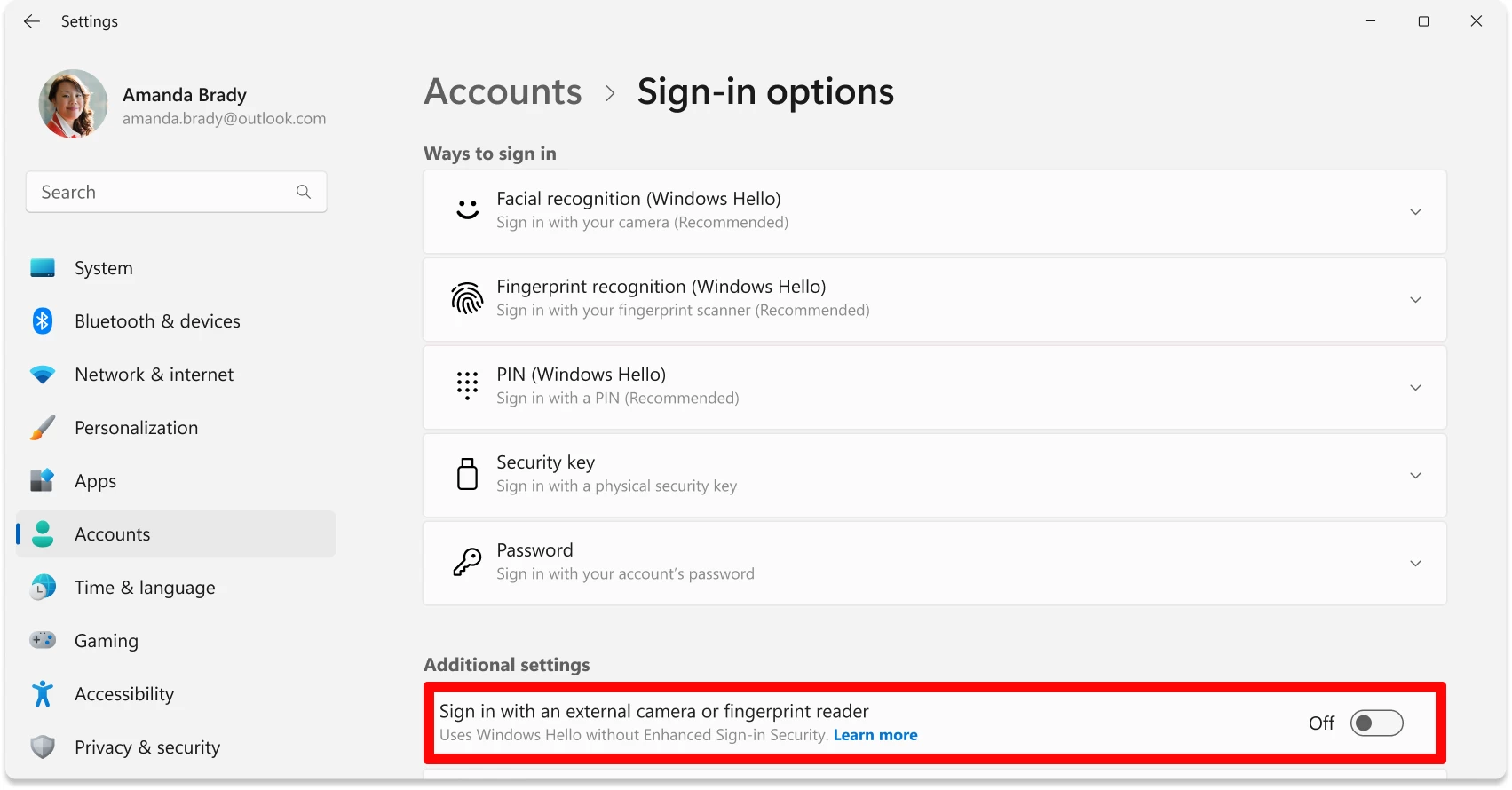
When that swap is off, ESS is lively, which additionally signifies that the USB fingerprint reader you obtain won’t work for logging into Home windows. Flip it on, and also you disable the characteristic, letting your exterior peripherals work at the price of that further safety.
Microsoft says that some “Home windows Hey suitable” peripherals can allow ESS in your system. Whereas this doesn’t pose a safety threat, it places you in a bind. The corporate means that in the event you should use one, you must plug it in earlier than the primary boot and principally by no means unplug it. Full, correct assist for exterior units with ESS shouldn’t be even anticipated till late 2025.




No Comment! Be the first one.