
Again in Might this yr, when Microsoft held its Construct 2025 convention, it launched NLWeb, quick for “Pure Language Net,” a venture that was meant to be a means for AI brokers to work together with web sites.
With firms like Shopify and TripAdvisor signed on, Microsoft pitched this as the muse for an “agentic internet,” a future the place AI brokers deal with advanced duties by speaking on to on-line providers.
Now, Aonan Guan, a safety researcher, alongside Lei Wang (by way of The Verge) have documented a path traversal vulnerability within the open-source framework. Based on Guan, they had been searching the NLWeb GitHub repo when a selected file caught their consideration: webserver/static_file_handler.py.
# The susceptible code snippet
safe_path = os.path.normpath(path.lstrip("
possible_roots = [
APP_ROOT,
os.path.join(APP_ROOT, 'site', 'wwwroot'),
'/home/site/wwwroot',
os.environ.get('HOME', ''),
]
# Later within the code...
full_path = os.path.be a part of(root, safe_path)
Should you check out the primary line of the code, you’d discover an harmless wanting line. From the official Python documentation, os.path.normpath() normalizes a pathname by collapsing redundant separators and up-level references.
On Home windows, it converts ahead slashes (/) to backslashes (). For instance, a path like A//B/./C/../D can be normalized to A/B/D, however this perform has a nasty aspect impact, as Guan notes. It doesn’t really forestall a person from “climbing” out of the meant internet listing utilizing ../ sequences.
Guan confirmed his suspicions when he arrange an area server listening on 0.0.0.0:8000, a regular testing configuration. When he ran curl "http://localhost:8000/static/..%2f..%2f..%2fetc/passwd", the server fortunately returned the contents of /and so forth/passwd.
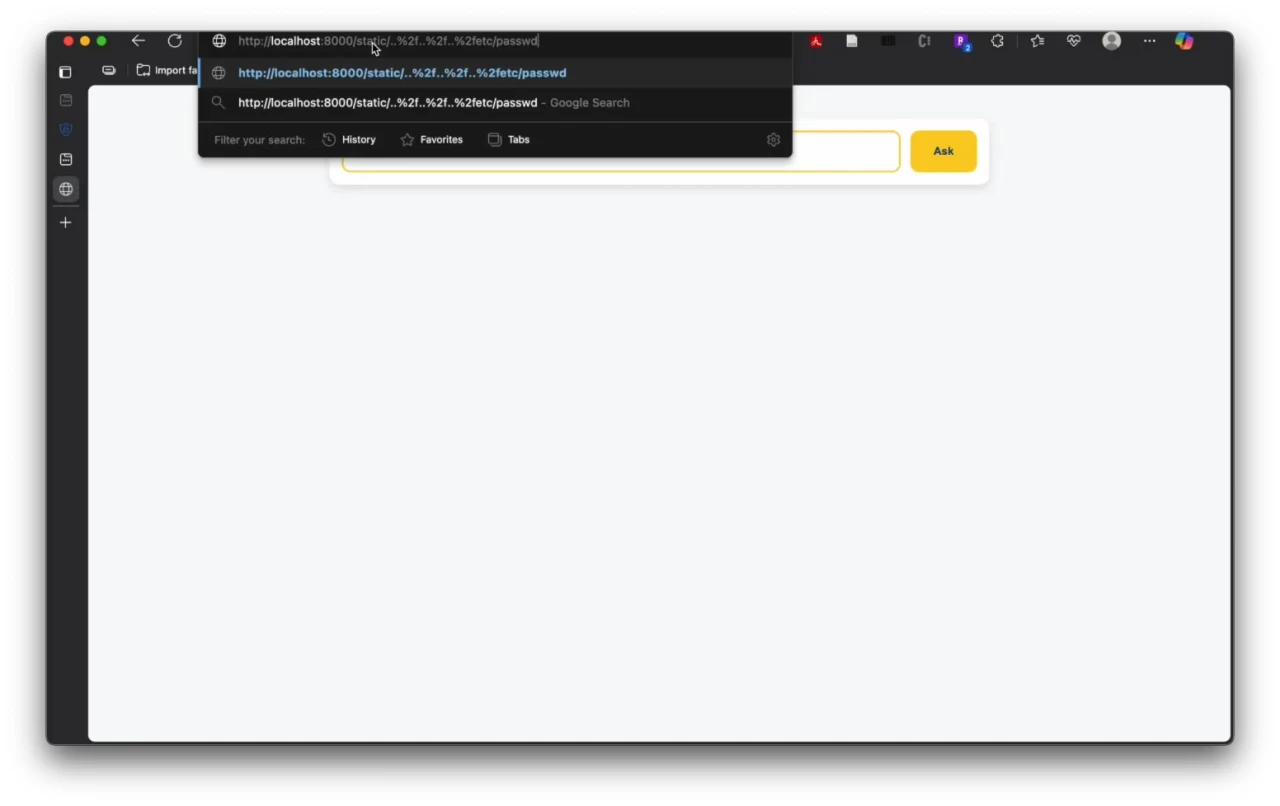
In case you might be unaware, /and so forth/passwd is the person account database on UNIX programs like Linux and macOS, the place it maps usernames to person IDs and different system data.
The researcher might additionally entry recordsdata inside the app’s supply code, together with the venture’s .env file (which it is best to by no means publicly expose because it accommodates secrets and techniques like API keys) when he ran curl "http://localhost:8000/static/..%2f..%2f..%2fUsers//NLWeb/code/.env".
The code did not sanitize person enter correctly in addition to validate that the ultimate, resolved file path was really contained in the designated internet root. Guan reported the vulnerability on Might twenty eighth. Microsoft acknowledged the report the identical day and issued a repair two days later.
Within the firm’s case, the repair was to first test for .. within the uncooked path to dam primary listing traversal makes an attempt. After that, it checks if the requested file ends with one of many allowed extensions: .html, .htm, .css, .js, .png, .jpg, .jpeg, .gif, .svg, .ico, .json, .txt, or .xml.
Lastly, and most significantly, it resolves the complete, absolute path of the requested file and confirms it resides inside one of many accredited root directories, stopping any escape.
Guan recommends updating your NLWeb occasion instantly and argues that this incident exhibits how the agentic internet introduces a brand new assault floor, since deciphering pure language from customers might inadvertently translate into malicious file paths or system instructions if not dealt with with excessive care.



No Comment! Be the first one.